This section is a part two series of Complete CI/CD Laravel Apps Using Gitlab CI To GKE. For those who haven’t read the previous article, please follow this link Complete CI/CD Laravel Apps Using Gitlab CI To GKE: Image Build.
SAST (Static Application Security Testing), is a tool that scans an application’s source, binary, or byte code. A white-box testing tool, it identifies the root cause of vulnerabilities and helps remediate the underlying security flaws.
Pros of SAST
- Scans source code to find weaknesses that lead to vulnerabilities
- Provides real-time reporting
- Cover languages that developers use
Cons of SAST
- Not capable of identifying vulnerabilities in dynamic environments
- High risk of reporting false positives
- Since the report is static, it becomes outdated quickly
In GitLab CI/CD, you can use Static Application Security Testing (SAST) to check your source code for known vulnerabilities. You can run SAST analyzers in any GitLab tier. The analyzers output JSON-formatted reports as job artifacts.
TLDR
- Add the following lines to your gitlab-ci.yaml file to activate the SAST scan on the pipeline
include:
- template: Jobs/SAST.gitlab-ci.yml
- template: Jobs/Secret-Detection.gitlab-ci.yml- To control what analyzers to be excluded please add the following variables to the gitlab-ci
SAST_EXCLUDED_ANALYZERS: "spotbugs, bandit, brakeman, gosec, semgrep, security-code-scan, flawfinder"- Then add the job for the SAST
## Example of sast job override
eslint-sast:
environment: code-scan
stage: test
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
expire_in: 1 day
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/
nodejs-scan-sast:
environment: code-scan
stage: test
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
expire_in: 1 day
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/- The full jobs on gitlab-ci for SAST Integration
variables:
SAST_IMAGE_SUFFIX: '-fips'
SAST_EXCLUDED_ANALYZERS: "spotbugs, bandit, brakeman, gosec, semgrep, security-code-scan, flawfinder"
stages:
- test
eslint-sast:
environment: code-scan
stage: test
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
expire_in: 1 day
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/
nodejs-scan-sast:
environment: code-scan
stage: test
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
expire_in: 1 day
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/
phpcs-security-audit-sast:
environment: code-scan
stage: test
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
expire_in: 1 day
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/
pmd-apex-sast:
environment: code-scan
stage: test
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
expire_in: 1 day
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/
secret_detection:
environment: code-scan
stage: test
variables:
CI_DEBUG_TRACE: "true"
artifacts:
name: secret_detection
paths:
- gl-secret-detection-report.json
reports:
secret_detection: gl-secret-detection-report.json
when: always
tags:
- mamad
when: manual
rules:
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)redeploy(?:$|\W)/
- if: $CI_COMMIT_TITLE =~ /(?:^|\W)code scan(?:$|\W)/
Pipeline Result
- SAST Test stage pipeline
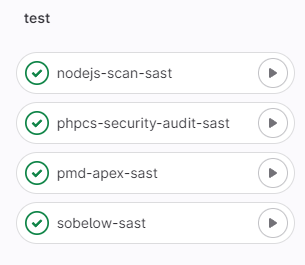
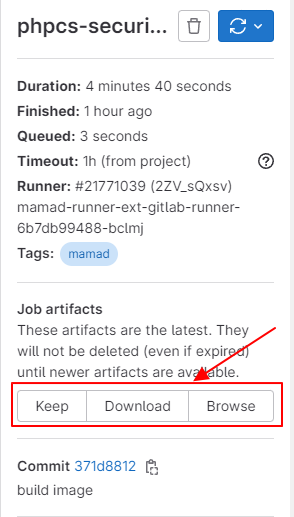
- Artifact report of the scan result
Conclusions
In this part, we have explained the pipeline and the SAST integration with GitLab CI on the built image.
In the next part, we will have an article to explain the continuous delivery integration to GKE using GitLab CI.
For more articles and tutorials please visit our website at settingserver.com.
If you have any more inquiries please reach out to us at [email protected]
Leave a Reply