ModSec / ModSecurity is a software package that creates a collection of regulations which can be employed as a Web Application Firewall (WAF) for the web server.
The WAF is responsible for managing access control, tracking usage, and observing incoming requests directed at specific web applications or web servers.
Having a WAF installed on the web server can reduce the risk of security threats, such as cross-site scripting, SQL injection, inclusion vulnerabilities, and brute force attacks.
Steps
Suppose you already have a Kubernetes cluster provisioned by RKE2.
- Create a new helm chart config with the example value below
apiVersion: helm.cattle.io/v1
kind: HelmChartConfig
metadata:
name: rke2-ingress-nginx
namespace: kube-system
spec:
valuesContent: |-
controller:
config:
use-forwarder-headers: true
enable-modsecurity: true
enable-owasp-modsecurity-crs: true
modsecurity-snippet: |
Include /etc/nginx/owasp-modsecurity-crs/custom/custom-modsecurity.conf
extraVolumeMounts:
- name: modsecurity-config
mountPath: /etc/nginx/owasp-modsecurity-crs/custom/
extraVolumes:
- name: modsecurity-config
configMap:
name: modsecurity-config
Explanation:
controller:
config:
# activate the x-forwarder nginx option
use-forwarder-headers: true
# activate the modsec and owasp rule
enable-modsecurity: true
enable-owasp-modsecurity-crs: true
# include the custom modsec rule to the destination path
modsecurity-snippet: |
Include /etc/nginx/owasp-modsecurity-crs/custom/custom-modsecurity.conf
# add extra option to the chart with a configMap mounting point
extraVolumeMounts:
- name: modsecurity-config
mountPath: /etc/nginx/owasp-modsecurity-crs/custom/
extraVolumes:
- name: modsecurity-config
configMap:
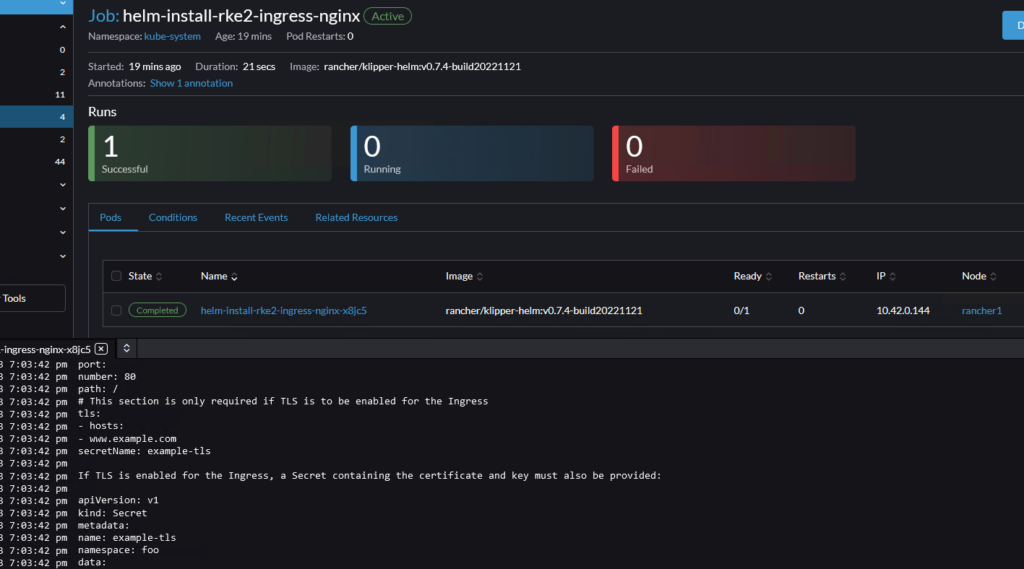
name: modsecurity-configapply the helm chart config above using a kubectl command:
kubectl apply -f /path/to/the/helmchartconfig.yaml
- Create a file for a custom ModSec rule, e.g
custom-modsecrule.conf
# By default is DetectionOnly. Can be any of: DetectionOnly,On,Off
SecRuleEngine On
# Avoid sending status information about ModSecurity in response header
SecStatusEngine Off
# Send ModSecurity audit logs to the stdout (only for rejected requests)
SecAuditLog /dev/stdout
SecAuditLogFormat JSON
SecAuditEngine RelevantOnly # could be On/Off/RelevantOnly
# Max request sizes in bytes (with/without files) - Note NGINX Ingress has its own parameter/annotation that should be kept in sync
SecRequestBodyLimit 20971520 # 20Mb (default is 12.5Mb)
SecRequestBodyNoFilesLimit 262144 # 250Kb (default is 128Kb)
SecRequestBodyLimitAction Reject # Reject if larger (we could also let it pass with ProcessPartial)
# recommended limits for regular expression recursion. See https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/656#issuecomment-262780221
SecPcreMatchLimit 500000
SecPcreMatchLimitRecursion 500000
# Include PUT/PATCH/DELETE in the allowed methods, otherwise those verbs will be rejected by rule 911100
SecAction "id:900200,phase:1,nolog,pass,t:none,\
setvar:tx.allowed_methods=GET HEAD POST OPTIONS PUT PATCH DELETE"
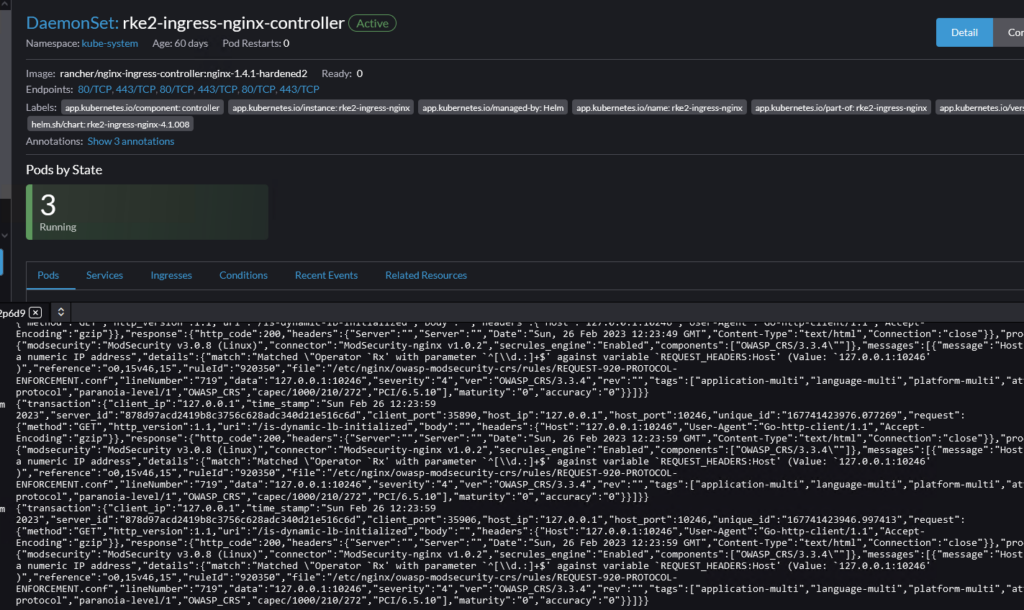
Result
Leave a Reply