Install Gitlab Kube Agent
To provide the Continues Delivery using GitLab, we need to install the agent into the GKE cluster.
The Installation steps are explained as the following:
- Optional. Create an agent configuration file.
- Register the agent with GitLab.
- Install the agent in your cluster.
Watch a GitLab 14.2 walk-through of this process
Agent Config and Deployment Strategy
- authorized your agent to access your project or a project group
ci_access:
projects:
- id: path/to/projectci_access:
groups:
- id: path/to/group/subgroup- Update your
.gitlab-ci.ymlfile to runkubectlcommands and set the context. Below is an example of the code
variables:
KUBE_AGENT_PATH: path/to/agent/repository
# Kube Prepare
.kube_prepare:
image:
name: bitnami/kubectl:1.26.1
entrypoint: ['']
before_script:
- ./pre_deploy.sh
- mkdir -pv ssl/
- cat "$FULLCHAIN" > ssl/fullchain.pem && cat "$PRIVKEY" > ssl/privkey.pem
- kubectl config use-context ${KUBE_AGENT_PATH}:${KUBE_AGENT_NAME}
- kubectl config set-context --current --namespace=${KUBE_NAMESPACE}
#Deploy to GKE Cluster
#Deploy to GKE Cluster
kube-deploy-prod-gke:
stage: deploy
environment:
name: production
on_stop: "Takedown Production GKE"
variables:
ENVIRONMENT: production
KUBE_ACTION2: delete
KUBE_ACTION: apply
MANIFEST_PATH: manifests-production-gke
NAMESPACE: $KUBE_NAMESPACE
APP_URL: travellist.ahmadcloud.my.id
CERT_NAME: star.ahmadcloud.my.id
tags:
- mamad
rules:
- if: $CI_COMMIT_TAG
- if: $CI_COMMIT_TITLE =~ /^redeploy/
- if: $CI_COMMIT_TITLE =~ /^gke deploy/
when: manual
extends: .kube_prepareThe script_deploy.sh is a helper to run a sum amount of kubectl command with bash unix syntaxis, while pre_deploy.sh is a script to replace relevant text with a specific name defined in the variable.
pre_deploy.shexample content
#!/bin/bash
sed -i "s|<image-tag-name>|$IMAGE_TAG1|g" $MANIFEST_PATH/deploy/deployments/*.yaml
sed -i "s|<APP_URL>|$APP_URL|g" $MANIFEST_PATH/deploy/configmap/*.yaml
sed -i "s|<APP_URL>|$APP_URL|g" $MANIFEST_PATH/deploy/ingresses/*.yaml && \
sed -i "s|<CERT_NAME>|$CERT_NAME|g" $MANIFEST_PATH/deploy/ingresses/*.yamlThe pre_deploy.sh has the goal to replace necessary string based on the variables defined on the .gitlab-ci.yaml or the GitLab CI/CD variables
script_deploy.shexample content
## Pre check
VALUE1=$(kubectl -n $NAMESPACE get pvc | awk '/^db/ {print $1}')
VALUE2=$(kubectl -n $NAMESPACE get pvc | awk '/^travellist/ {print $1}')
# Main Deploy Script
# Deploy Conditions
if [[ "$ENVIRONMENT" == "production" ]]; then
kubectl "$KUBE_ACTION" -f "$MANIFEST_PATH"/namespace/ --recursive;
kubectl -n $NAMESPACE create secret generic database --from-file=user_password=$USER_PASSWORD
kubectl -n $NAMESPACE create secret docker-registry gcr-io \
--docker-server asia.gcr.io \
--docker-username _json_key \
--docker-email [email protected] \
--docker-password="$(echo $GCR_JSON)"
kubectl -n $NAMESPACE create secret tls "$CERT_NAME" \
--cert=ssl/fullchain.pem \
--key=ssl/privkey.pem
if [[ $VALUE1 != *db* || $VALUE2 != *travellist* ]]; then
kubectl "$KUBE_ACTION" -f "$MANIFEST_PATH"/pvcs/ --recursive;
fi
kubectl "$KUBE_ACTION2" -f "$MANIFEST_PATH"/deploy/statefulsets/ --recursive && sleep 1;
#kubectl "$KUBE_ACTION2" -f "$MANIFEST_PATH"/deploy/deployments/ --recursive && sleep 1;
kubectl "$KUBE_ACTION" -f "$MANIFEST_PATH"/deploy/ --recursive;
elif [[ "$ENVIRONMENT" == "staging" ]]; then
kubectl "$KUBE_ACTION" -f "$MANIFEST_PATH"/namespace/ --recursive;
if [[ $VALUE1 != *db* || $VALUE2 != *travellist* ]]; then
kubectl "$KUBE_ACTION" -f "$MANIFEST_PATH"/pvcs/ --recursive;
fi
kubectl -n $NAMESPACE create secret generic database --from-literal=user_password=$USER_PASSWORD
kubectl -n $NAMESPACE create secret tls "$CERT_NAME" \
--cert=ssl/fullchain.pem \
--key=ssl/privkey.pem
kubectl "$KUBE_ACTION2" -f "$MANIFEST_PATH"/deploy/statefulsets/ --recursive && sleep 1;
#kubectl "$KUBE_ACTION2" -f "$MANIFEST_PATH"/deploy/deployments/ --recursive && sleep 1;
kubectl "$KUBE_ACTION" -f "$MANIFEST_PATH"/deploy/ --recursive;
fiThe script_deploy.sh has the following goals:
- Create secrets (database password, private docker secret, and TLS) to the k8s environment
- Apply necessary manifest files to the k8s cluster
- Create necessary PVCs based on the parameter check
Result
Pipeline Result
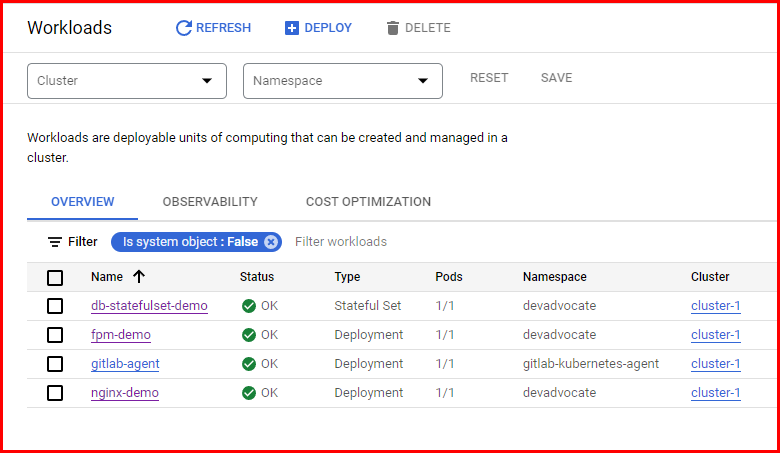
Deployment Result
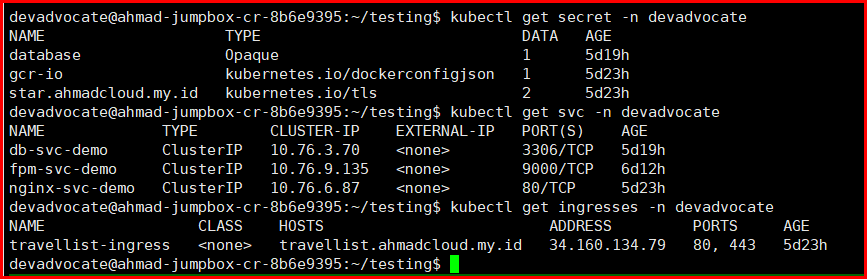
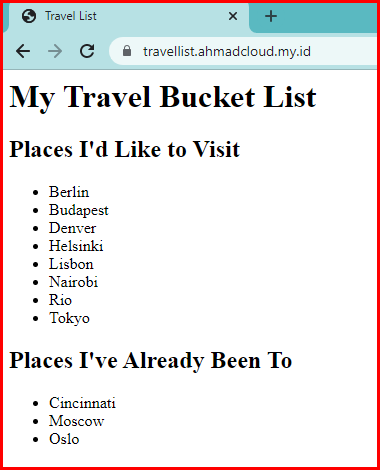
Test Result
Leave a Reply